Computer networks miscellaneous
Direction: Consider a network with five nodes, N1 to N5, as shown below :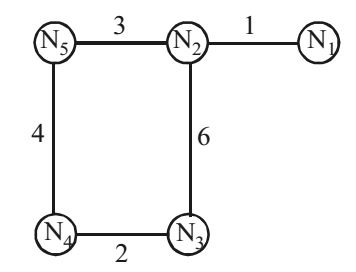
The network uses a distance vector routing protocol. Once the routes have stabilized, the distance vectors at different nodes are as following. Each distance vector is the distance of the best known path at that instance to nodes, N1 to N5, where the distance to itself is 0. Also, all links are symmetric and the cost is identical in both directions. In each round, all nodes exchange their distance vectors with their respective neighbours, Then all nodes update their distance vectors. In between two rounds, any change in cost of a link will cause the two incident nodes to change only that entry is their distance vectors.
- The cost of link N2 -N3 reduces to 2 in (both directions). After the next round of updates, what will be the new distance vector at node N3?
-
View Hint View Answer Discuss in Forum

Distance vector for N3 will be
N3 : (N1, N2, N3, N4, N5)
N3 : (3, 2, 0, 2, 5)Correct Option: A

Distance vector for N3 will be
N3 : (N1, N2, N3, N4, N5)
N3 : (3, 2, 0, 2, 5)
Direction: Consider a network with 6 routers R1 to R6 connected with links having weights as shown in the following diagram.
- Suppose the weights of all unused links in the previous question are changed to 2 and the distance vector algorithm is used again until all routing tables stabilize. How many links will now remain unused?
-
View Hint View Answer Discuss in Forum
As in the previous question
 and
and  not used. So, we give them weight = 2, by applying same method only one link not used.
not used. So, we give them weight = 2, by applying same method only one link not used.Correct Option: B
As in the previous question
 and
and  not used. So, we give them weight = 2, by applying same method only one link not used.
not used. So, we give them weight = 2, by applying same method only one link not used.
- All the routers use the distance vector based routing algorithm to update their routing tables. Each router starts with its routing table initialized to contain an entry for each neighbour with the weight of the respective connecting link. After all the routing tables stabilize, how many links in the network will never be used for carrying any data?
-
View Hint View Answer Discuss in Forum
We can check one by one all shortest distances. When we check for all shortest distances for Ri we don't need to check its distances to R0 to Ri-1 because the network graph is undirected.
Following will be distance vectors of all nodes.
Shortest Distances from R1 to R2, R3, R4, R5 and R6 R1 (5, 3, 12, 12, 16)
Links used : R1-R3, R3-R2, R2-R4, R3-R5, R5-R6
Shortest Distances from R2 to R3, R4, R5 and R6 R2 (2, 7, 8, 12)
Links used : R2-R3, R2-R4, R4-R5, R5-R6
Shortest Distances from R3 to R4, R5 and R6 R3 (9, 9, 13)
Links used : R3-R2, R2-R4, R3-R5, R5-R6
Shortest Distances from R4 to R5 and R6 R4 (1, 5)
Links used : R4-R5, R5-R6
Shortest Distance from R5 to R6 R5 (4)
Links Used : R5-R6
If we mark, all the used links one by one, we can see that following links are never used.
R1-R2
R4-R6Correct Option: C
We can check one by one all shortest distances. When we check for all shortest distances for Ri we don't need to check its distances to R0 to Ri-1 because the network graph is undirected.
Following will be distance vectors of all nodes.
Shortest Distances from R1 to R2, R3, R4, R5 and R6 R1 (5, 3, 12, 12, 16)
Links used : R1-R3, R3-R2, R2-R4, R3-R5, R5-R6
Shortest Distances from R2 to R3, R4, R5 and R6 R2 (2, 7, 8, 12)
Links used : R2-R3, R2-R4, R4-R5, R5-R6
Shortest Distances from R3 to R4, R5 and R6 R3 (9, 9, 13)
Links used : R3-R2, R2-R4, R3-R5, R5-R6
Shortest Distances from R4 to R5 and R6 R4 (1, 5)
Links used : R4-R5, R5-R6
Shortest Distance from R5 to R6 R5 (4)
Links Used : R5-R6
If we mark, all the used links one by one, we can see that following links are never used.
R1-R2
R4-R6
- An IP router implementing Classless Inter-domain Routing (CIDR) receives a packet with address 131.23.151.76. The router’s routing table has the following entries :

The identifier of the output interface on which this packet will be forwarded is ______.
-
View Hint View Answer Discuss in Forum
Address 131.23.151.76
Coming to I field of given routing table.
⇒ 131.16.0.0/12
131.0001 0111.151.76
131.0001 0000.0.0 (mask bit = 12)
131.16.0.0 (matched)
Coming to II field of given routing table.
⇒ 131.28.0.0/14
131.0001 0111.151.76
131.0001 0100.0.0 (mask bit = 14)
131.20.0.0 (not matched)
Coming to III field of given routing table
⇒ 131.19.0.0/16
131.0001 0111.151.76
131.0001 0111.0.0 (mask bit = 16)
131.23.0.0 (not matched)
Coming to IV field of given routing table
⇒ 131.22.0.0/15
131.0001 0111.151.76
131.0001 0110.0.0 (mask bit = 15)
131.22.0.0 (matched)
∵ I and IV entries are matched, we pickup longest mask bit
∴ Output interface identifies is 1.Correct Option: B
Address 131.23.151.76
Coming to I field of given routing table.
⇒ 131.16.0.0/12
131.0001 0111.151.76
131.0001 0000.0.0 (mask bit = 12)
131.16.0.0 (matched)
Coming to II field of given routing table.
⇒ 131.28.0.0/14
131.0001 0111.151.76
131.0001 0100.0.0 (mask bit = 14)
131.20.0.0 (not matched)
Coming to III field of given routing table
⇒ 131.19.0.0/16
131.0001 0111.151.76
131.0001 0111.0.0 (mask bit = 16)
131.23.0.0 (not matched)
Coming to IV field of given routing table
⇒ 131.22.0.0/15
131.0001 0111.151.76
131.0001 0110.0.0 (mask bit = 15)
131.22.0.0 (matched)
∵ I and IV entries are matched, we pickup longest mask bit
∴ Output interface identifies is 1.
- An IP router with a Maximum Transmission Unit (MTU) of 1500 bytes has received an IP packet of size 4404 bytes with an IP header of length 20 bytes. The values of the relevant fields in the header of the third IP fragment generated by the router for this packet are
-
View Hint View Answer Discuss in Forum


Correct Option: A



